AI techniques are evolving sooner than most safety applications can monitor. Fashions change, instruments multiply, and agent behaviors emerge throughout codebases and containers. That creates a easy however pressing query: what’s an AI system composed of and the way is it constructed?
The reply to that’s Cisco’s AI BOM (AI Invoice of Supplies), now obtainable as a part of Cisco AI Protection and as an open-source software. It provides safety and engineering groups a transparent stock of AI belongings and the context wanted to know how these AI belongings are orchestrated in an agentic workflow.
The AI Stock Hole
Conventional SBOM (Software program Invoice of Supplies) focuses on packages and dependencies. Then again, cloud visibility platforms present visibility into deployed infrastructure on cloud, which can embrace AI belongings, corresponding to fashions, MCP instruments, brokers, and prompts. That isn’t sufficient for complete AI visibility. For instance, an AI chat app might connect with a number of brokers, use a number of MCP instruments, and different MCP constructs and datastores like vector databases to construct a cohesive response to consumer queries. Organizations want deep visibility into AI-specific constructing blocks like fashions, brokers, instruments, prompts, and the workflows that connect with them by shifting left to the supply of the AI app by scanning the code in code repositories or container photographs to provide a complete AI BOM.
With out that deep visibility, groups face AI provide chain dangers like:
- Unapproved or surprising fashions launched into manufacturing
- Shadow instruments or agent capabilities that develop past supposed scope
- AI workflows that contact delicate knowledge with out clear lineage
- Incomplete governance and audit trails for AI techniques
Cisco’s AI BOM: A Differentiated Method
Cisco’s AI BOM is purpose-built to map the AI belongings used within the AI utility. In its preliminary launch, it scans codebases and container photographs to establish AI belongings like brokers, prompts, fashions, and instruments to provide a structured report of how these AI belongings are used collectively. This lays the muse for deeper lineage and dependency evaluation.
Cisco’s AI BOM’s method facilities on three rules:
- AI asset discovery
This focuses on AI belongings that matter to safety and governance, not simply generic dependencies. Conventional SBOMs have centered on bundle dependencies utilized in a software program product. - A curated information base
It’s powered by information base which is often up to date with a complete categorization of all code constructs, together with greater than 10+ standard AI and agentic frameworks like Langchain, OpenAI, AWS BedRock, Autogen, Anthropic SDK, and Google GenAI to a point out just a few. This gives beneficial grounding info to map AI belongings found in supply code. - AI asset dependency graph
AI BOM constructs dependency graphs that present how AI belongings are orchestrated inside an AI utility. This contains relationships between brokers, fashions, MCP instruments and prompts, primarily based on code scans.
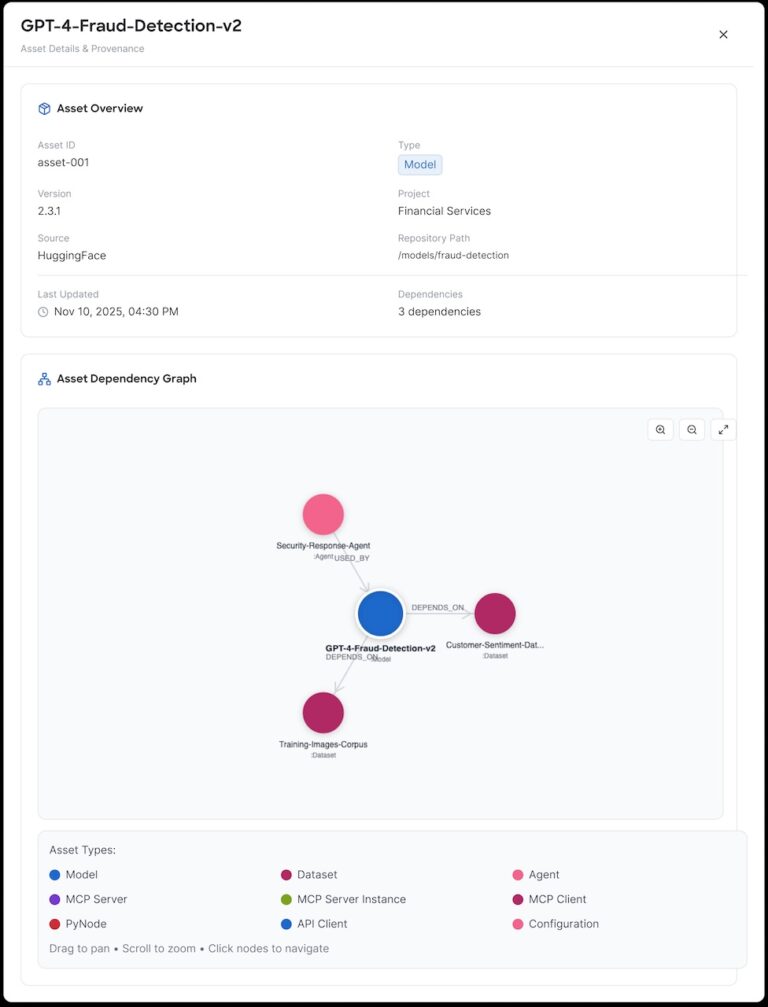

This mixture makes AI BOM uniquely actionable. It reveals what belongings are there, how they’re utilized by AI functions, and the place they sit in your AI ecosystem.
Cisco’s Method to AI Safety
Cisco AI Protection secures the AI utility lifecycle by way of a unified method spanning Discovery, Detection, and Safety.
Securing AI utility lifecycle utilizing AI Protection begins with discovery which focuses on figuring out AI belongings and understanding how they’re used. AI Protection gives AI cloud visibility throughout fashions, brokers, and linked knowledge sources. AI-BOM augments this discovery by figuring out how AI functions are constructed from supply code and container photographs, capturing visibility into AI belongings corresponding to fashions, brokers, MCP instruments, and frameworks.
Detection makes use of this asset visibility to establish danger earlier than manufacturing impression. AI Protection scans mannequin information, brokers, prompts and MCP instruments to detect malicious or unsafe AI belongings as a part of AI provide chain danger administration. It additionally runs algorithmic purple teaming by way of AI Validation, that identifies security, safety, and privateness vulnerabilities in AI belongings and functions.
Safety mitigates threats at runtime. With full visibility into AI belongings, AI Protection Runtime applies guardrails to manufacturing AI functions and brokers, blocking dangerous responses and assaults in actual time to guard deployed AI functions. Collectively, these capabilities assist groups transfer past ad-hoc audits towards constant, repeatable AI safety practices throughout the AI utility lifecycle.
Get Began
Cisco’s AI BOM is an open-source, CLI-based utility obtainable now for early experimentation, extension and integration into developer workflows. Discover the venture, evaluate the method, and contribute to the group on the GitHub repository: https://github.com/cisco-ai-defense/aibom

