Going through an ever-evolving and more and more subtle cybersecurity panorama, organizations have a urgent want to achieve higher visibility of and insights into their community visitors. Most threats are delivered over encrypted channels, rising the necessity to examine encrypted visitors traversing the community to search for doable obscured threats.
In Cisco Safe Firewall model 10.0, our most up-to-date software program launch, we’ve delivered 4 compelling new options to assist clients shortly and effectively assess and act on data of their community visitors. You possibly can check drive these capabilities at this time with Safe Firewall Take a look at Drive, an teacher led course that may information you thru the Safe Firewall and its highly effective roles in cybersecurity to your group.
Simplified decryption
The easiest way to achieve visibility into encrypted visitors is to decrypt it. The brand new simplified decryption expertise in Cisco Safe Firewall model 10.0 simplifies the steps required to allow and handle encryption. As a substitute of a standard rules-based design, Straightforward Decrypt permits quick creation of inbound and outbound decryption insurance policies by focusing on inner servers by way of any sort of community object.
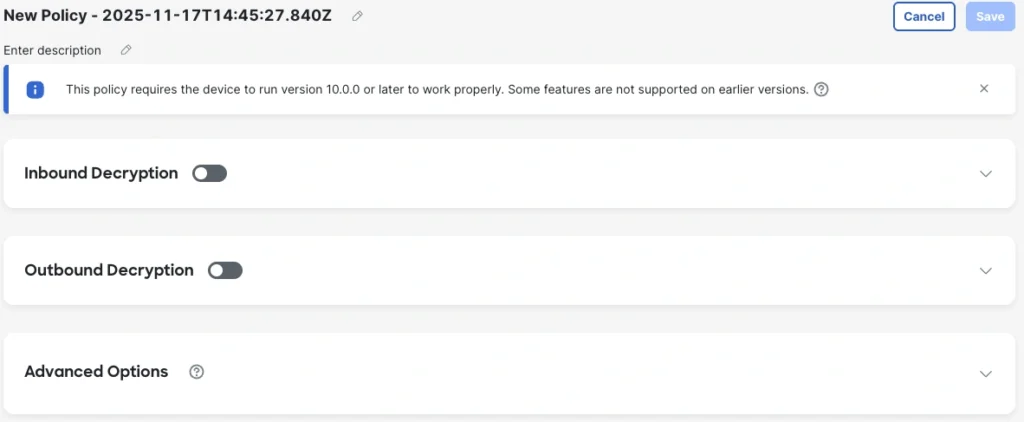

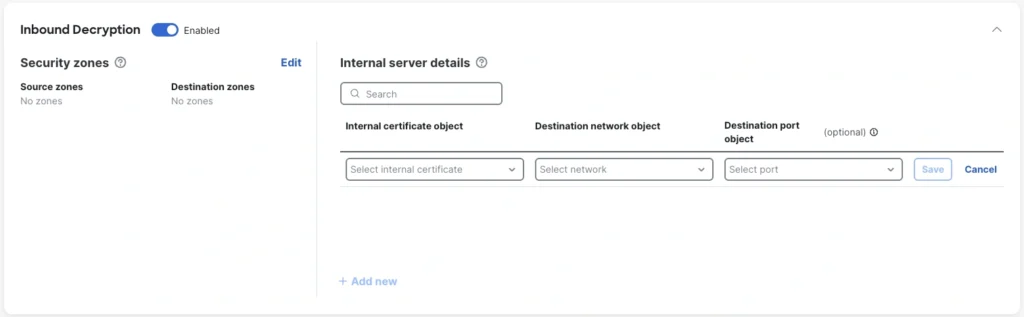

Moreover, certificates are individually selectable for every server. The general public-facing certificates may be serviced by Let’s Encryptconsiderably decreasing certificates upkeep overheads. Outbound decryption certificates administration can now be managed proper from the decryption coverage web page, making for a better workflow when constructing out insurance policies.
All object varieties supported for decryption insurance policies embrace key attributes similar to absolutely certified area identify (FQDN), URL, community and community teams and ranges, supply group tags, dynamic objects, and extra.
To ease selective decryption as wanted, the Cisco-provided AppID bypass checklist permits excluding entries from this checklist for decryption. The earlier launch of Cisco Safe Firewall launched Clever Decryption Bypass, additional easing determination making round which visitors to decrypt by assessing low-risk visitors that’s probably protected to bypass decryption processes. It determines what visitors is low threat by combining information from Talos fame scores and the shopper risk confidence rating offered by the Encrypted Visibility Engine (EVE).
Lastly, all new guidelines are routinely enabled for complete logging to supply higher visibility into guidelines’ utilization and any potential issues inside the community.
QUIC decryption
Fast UDP Web Connections (QUIC) is a natively encrypted safe protocol designed to extend the pliability and efficiency of internet purposes whereas additionally bolstering safety. Nonetheless, additionally it is harder to achieve visibility into this visitors, because the transport expertise is totally different from conventional TCP-encrypted visitors. QUIC as a substitute depends upon Person Datagram Protocol (UDP) transport and straight implements TLS 1.3 into the session handshake, permitting encryption of handshake messages after the primary packet. Whereas TCP+TLS encryption left handshake messages clear to inspection, virtually all handshake information after the primary packet is hidden with QUIC. Even the Server Identify Indicator (SNI), which specifies the server the shopper is speaking with, may be encrypted by implementing Encrypted Consumer Hi there (ECH) alongside QUIC.
A number of obfuscations inside QUIC make it troublesome to hint or observe a full QUIC session, similar to:
- Sequence numbering within the header is encrypted
- No TCP metadata exists, similar to for SYN, ACK, FIN, RST messages
- Multiplexed streams are hidden contained in the encryption
- The connection may be migrated throughout IP addresses with out transport header indication
The specific goal of QUIC is to go away solely the important data a router or related gadget requires to transmit and ahead packets, however this objective runs opposite to the safety and accountability objectives of many organizations.
QUIC adoption is on the rise amongst international internet visitors, rising from about 7% utilization in 2020 to round 45% utilization in 2025. A couple of third of all internet providers and over 80% of Google providers at the moment are QUIC-first (that’s, providers the place QUIC is obtainable earlier than TCP+TLS).
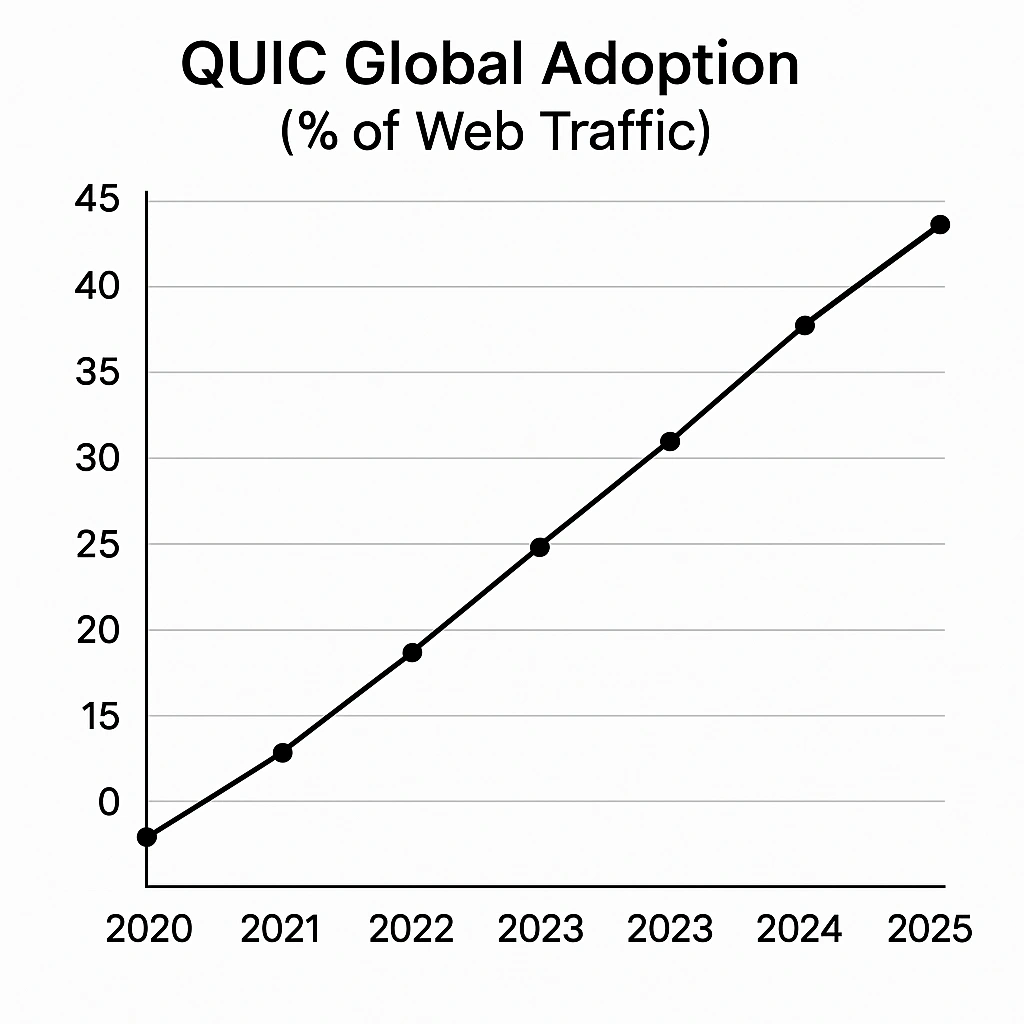

Contemplating this rising adoption and the necessity for higher visibility and management the place the QUIC protocol is in use, decryption insurance policies in Cisco Safe Firewall model 10.0 have been enhanced to permit decryption and inspection upon QUIC visitors to make sure visibility is maintained whereas benefiting from the enhancements supplied by this protocol.
In environments and use circumstances the place decryption of QUIC visitors isn’t doable, the Encrypted Visibility Engine (EVE) offers extremely correct fingerprinting of QUIC visitors that uniquely characterizes and analyzes QUIC-encrypted classes to evaluate post-exploit beaconing and related suspicious visitors. This compelling functionality helps be sure that all organizations can achieve perception and protections for QUIC visitors because the utilization of this protocol will increase.
Shadow visitors reporting
Some strategies supplied by privateness applied sciences trigger a lack of visibility inside organizational networks. This assortment of recent “Lack of Visibility” stories focuses on these circumstances, providing statistical and detailed stories to assist establish visitors the place safety evaluation is incomplete attributable to obfuscations between the supply and vacation spot.
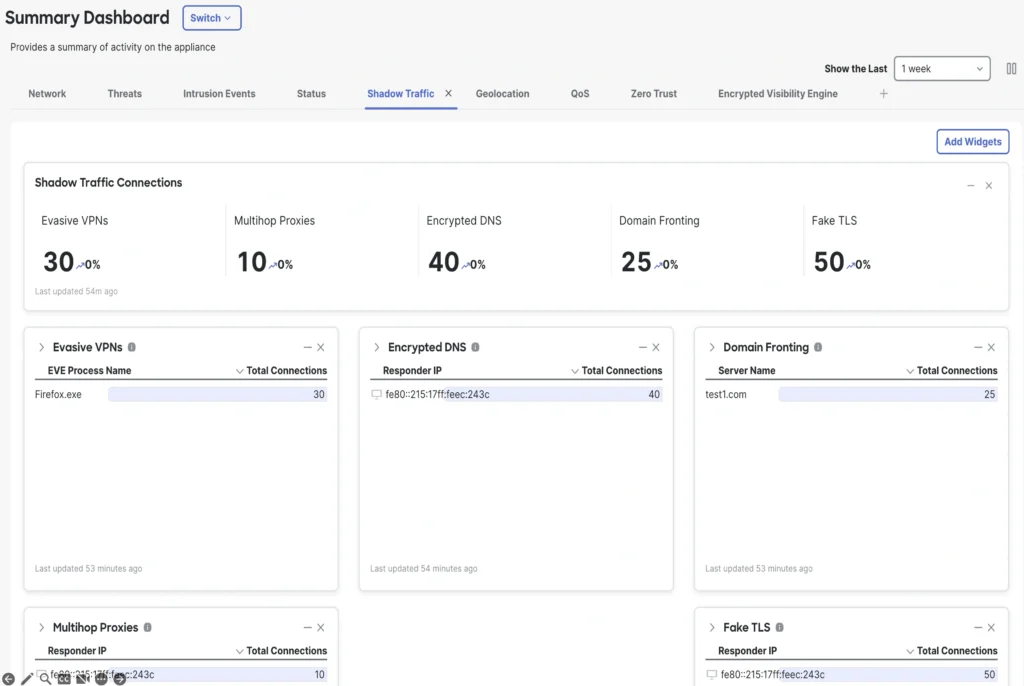

Included “Lack of Visibility” stories
Multihop proxies: Site visitors passing from a shopper to a proxy that in flip passes to a number of proxies turns into troublesome to hint to origin and will point out an try to cover assault makes an attempt.
Encrypted DNS: If area identify lookup data isn’t accessible, then insurance policies proscribing sure domains don’t take impact as anticipated.
Pretend TLS: Some visitors comprises TLS handshakes, headers, or different implementations that point out TLS encryption is employed whereas not truly conforming to the protocol, as a substitute offering a route for malware assaults, command and management beaconing, or tunneling non-encrypted visitors.
Evasive VPN: Some VPN providers deliberately conceal alerts indicating their use by means similar to visitors masking or obfuscating the protocols used for the visitors. When evasive VPNs are detected, the appliance making the evasive connections is recognized within the Shadow Site visitors view, permitting for easy coverage creation to dam that course of.
Area fronting: Some connections will promote broadly trusted entrance domains within the SNI, then use a unique HTTP host header contained in the encrypted connection to direct visitors to a unique backend service on the identical supplier. This could trigger guidelines that permit broadly trusted domains to have unintended unintended effects, permitting visitors that’s not fascinating. These domain-fronting URLs are displayed within the Shadow Site visitors view to focus on the place coverage selections could have to be made.
Moreover, it’s now simpler to modify configurations to disallow these applied sciences the place desired.
Superior logging
To reinforce the already strong set of data accessible for logged connections inside Cisco Safe Firewall and Cisco Safe Community Analytics, a brand new log sort has been created and made searchable. Traits logged embrace:
Software metadata: Establish suspicious purposes or tried misuses of recognized purposes with publicity to the metadata pertaining to that software
Clever PCAPs: Detailed packet information to facilitate deep forensics of safety occasions
Deeper insights on layer 5-7 connections: This concentrate on extra detailed details about session, presentation, and software layer visitors offers extra complete visibility into application-level actions to research breaches even the place community degree visitors appears benign or trusted
HTTP, FTP, DNS, and connection logging: By detailing internet, file switch, area lookup, and normal connection information, higher context is on the market for nearer investigations of safety occasions
Bizarre logging: Capturing protocol deviations and strange community behaviors alert safety groups to visitors which will sign novel assaults or misconfigurations inside purposes and networks
Discover logging: Particularly, security-relevant occasions are grouped and surfaced to help in risk searching and evaluation
This enhanced information helps community and safety directors perceive extra concerning the visitors of their group’s community and make knowledgeable coverage selections and suggestions.
Splunk correlation with superior logging
The deeper insights in superior logging permit for Splunk correlations to current Cisco Safe Firewall logs and occasions, in addition to different community and safety logs and information inside organizational environments and monitored by the group’s Splunk occasion. These correlations supply alternatives to extra shortly detect, triage, and create responses to safety occasions by streamlining efforts to hint the occasion by the community and discover further alerts to grasp the occasion’s influence.
Take a hands-on look at Cisco Safe Firewall 10.0
Wish to dive deeper into Cisco firewalls? Join the Cisco Safe Firewall Take a look at Drivean instructor-led, 4-hour hands-on course the place you’ll expertise the Cisco firewall expertise in motion and study concerning the newest safety challenges and attacker strategies.
We’d love to listen to what you assume! Ask a query and keep related with Cisco Safety on social media.
Cisco Safety Social Media

